A lot has changed since I wrote the First part of phishing with EV and this is the right time to release the final part of this series. Let’s get on.
A few weeks after the release of the first part of this series, a discussion started on the CA/Browser Forum public list and a few methods were discussed such as face to face validation, etc. There was some resistance to the discussion by some as they felt that the EV guidelines were rigid enough and didn’t need to be revisited. Nothing really came from the discussions, expect the CA/Browser Forum validation working group is going to investigate the matter further.
A few weeks after this discussion, Ian Carroll published an article named “Extended Validation is Broken” and this article demonstrated an easy way to obtain an EV certificate for phishing. In a nutshell, every US state operates an independent company registrar and as such, this means that incorporating a company in Delaware doesn’t give that company exclusive rights to that name in other states and as such someone else can incorporate the same name in another state such as the state of Kentucky.
EV certificates have not materially updated their requirements in 12 years and have not attempted to address core issues such as colliding names, and as a result, over time the browsers have been removing detail from the EV indicator which only masks the problem as this incident shows.
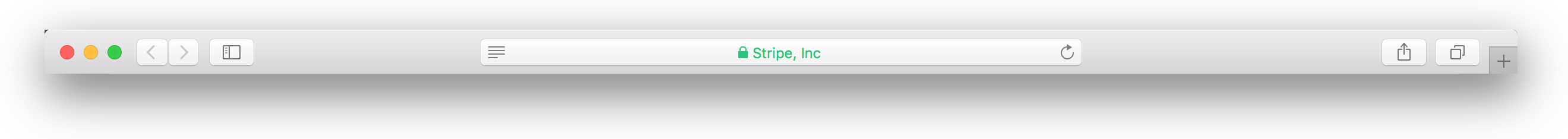
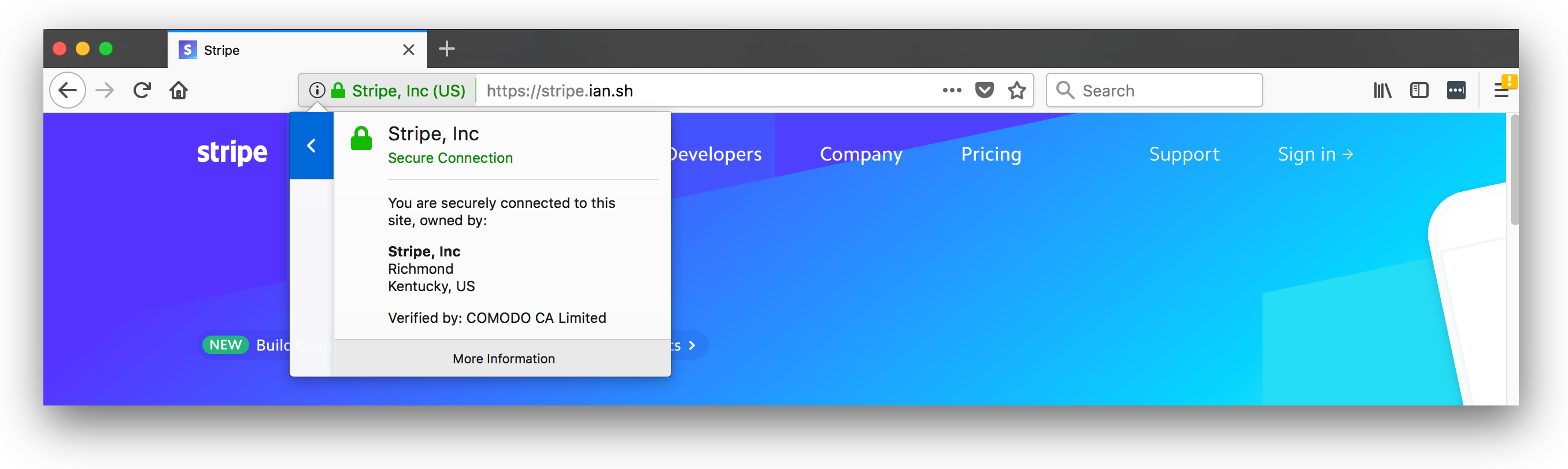
As a result of this inaction, both Ian’s “Stripe, Inc” and the “Stripe, Inc” the payment company are represented with the same in the security indicator. The only way to tell the difference is to navigate to the certificate details tab (if present) and closely inspect the details. No one does this, so it’s a perfect illusion.
What I describe above is precisely what Ian did with “Stripe, Inc”, he incorporated the company in the state of Kentucky which as you can see is exactly the same company name as the payment provider “Stripe, Inc” is incorporated in the state of Delaware.
Though Ian’s project was clearly in the name of research it is also important to keep in mind that there is a legitimate business need for multiple entities to share the same name. For example, there could be a “Stripe, Inc” that offers pavement striping services and they too should be able to get an EV certificate for their site.
He then went to Comodo and got an EV certificate for “Stripe, Inc” and see the results for yourself. It’s stunning.
I would like to thank Ian Carroll for taking the time to do this research,
After the release of Ian’s article, more discussions took place and the press started looking into both pieces and all this gathered more traction but still, nothing changed with EV.
Five months later and out of the nowhere, Comodo revokes the “Stripe, Inc” EV certificate and states that the EV certificate was revoked for being misleading and fraudulent. On top of this, Comodo initially refused to provide Ian with his money back. Thankfully he did ultimately manage to get his money back when it became public.
A month goes by and Ian manages to get another EV certificate from GoDaddy for “Stripe, Inc”. Everything is going well until GoDaddy revokes this EV certificate hours later. Why? Supposed “Fraud” reasons.
Both Comodo and GoDaddy should never have revoked these EV certificates, there was nothing on the site which was misleading or fraudulent, the information included in the certificate was factual and in compliance with the requirements of the EV Guidelines. This was an educational site showing one of the ways that EV is broken.
Another month goes by and Comodo releases a public statement apologising to Ian for revoking “Stripe, Inc” EV certificate and everything is looking up. First time ever a CA has apologized for making a mistake. Great!
Before I continue further, I’m going to clear up some points which I didn’t express properly in the first part of this series.
The company “Identity Verified” is a legitimate incorporated company in the UK. The company type is a limited company by guarantee with the “limited” exemption. This means that I don’t have to include the word “limited” at the end of the company name.
This company was incorporated using a legitimate address and identification. You can view the Companies House incorporation document here.
After the announcement from Comodo, I decided to try again and found out if they would actually issue the EV certificate for “Identity Verified” I went on the CertCenter site, a Comodo reseller, and ordered a standard EV certificate and after a few hours it was issued.

I quickly installed the EV certificate on sirburton.com since from my previous experiences I know CAs are known for changing their minds quickly and for revoking certificates and left, right and centre. Then the news came.
Comodo sent an email informing me that they’ve revoked the EV certificate and that I should contact CertCenter and request a refund. Now, at the time I was incredibly busy and didn’t check my inbox at all. Once I became aware some two hours later, I promptly sent an email asking “Why was the certificate revoked?” and the response I received was abysmal. Let’s not beat around the bush here, the whole email thread was deplorable. The only meaningful information I got was “compliance issues”. What does this mean? What do I need to do to address these “compliance issues”? Do I need to get a magic ball? Ridiculous!
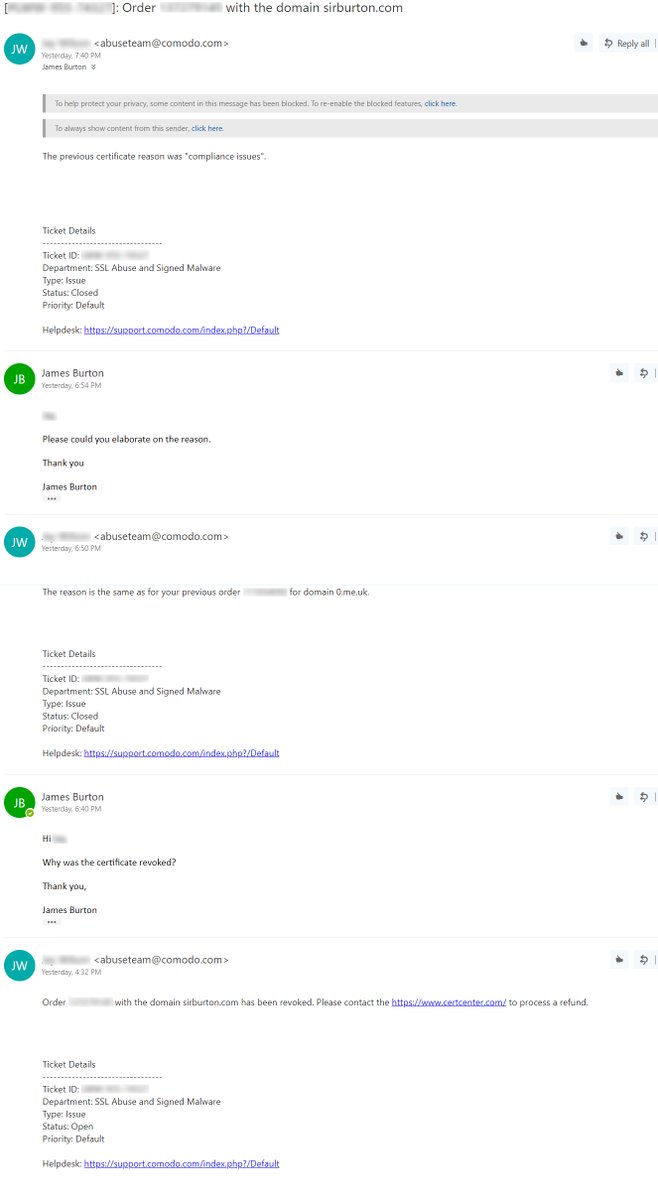
I decided that the best course of action is now to publicly tweet out the emails (name and order number blurred out) and get the community on board and this will entice Comodo to respond back with a better explanation which they did. I’ve copied and put Comodo’s response in this post and in italic to make sure they can’t be deleted later.
“.@troyhunt and @sirjamesburton Comodo CA’s subscriber agreement (https://bit.ly/2rvuEpH ), allows revocation if “information in the certificate is inaccurate or misleading” (3 (iv)). (1/3)”
“Our validators felt that the company name could easily be misinterpreted by users and that under the circumstances revocation was in online community’s best interest. (2/3)”
“The certificate world is always in flux and CAs’ practices & policies must respond to change. We want to engage the greater community to ensure we are accounting for these viewpoints as we evolve. James, If you disagree with this, we are open to hearing your rationale. (3/3)”
Section 3, paragraph IV:
“The Certificate has been 1) misused, 2) used contrary to law, rule, or regulation or 3) used, directly or indirectly, for illegal or fraudulent purposes;”
There is nothing in paragraph 3(IV) that substantiates the basis of revoking this EV certificate. It hasn’t been misused, hasn’t been used for unlawful or harmful purposes. So, what am I missing? Nothing.
The company name “Identity Verified” itself could be used to give the illusion that the website is indeed safe and trustworthy, but I think we’ve been looking at this situation from the wrong way.
There are lots of ways one can use an EV certificate for harmful purposes and mine and Ian’s research do not even cover half of it. Gerv Markham gave a wonderful alternative scenario:
“If you want an alternative scenario to use mentally, how about the scenario of a fly-by-night internet shop, set up with an EV certificate in the run-up to Christmas, which spends a week taking people's money and then disappears with it before people realize nothing is shipping.”
I think this says it all. EV can’t be relied on to protect users against harm. There is no fundamental difference between EV and DV expect for the green bar. Users are not at all good at properly differentiating the real sites from the fraudulent sites and that why we’ve got other methods such as Google Safe Browsing and Microsoft SmartScreen.
Coming back to whether Comodo should have revoked this certificate and the answer is profoundly NO, Why? Everything has risk and risk is part of the game of being a CA. CAs shouldn’t be allowed to pick or choose who they issue a certificate to as they are here for public good and restricting certificate issue based on content goes against the very foundations of the web.
“The original idea of the web was that it should be a collaborative space where you can communicate through sharing information. -- Tim Berners-Lee”
CAs can lower this risk be enhancing their vetting procedures and what I mean by that is require additional documentation from the customer such as identity documentation of the requestor, business bank statements, a signed accountant letter, etc.
The intelligence services do this for different categories of classified material and these categories are SECRET, TOP SECRET, and STRAP. To make sure that these individuals can be trusted with this material they are vetted to a certain level and these levels are as follows: Counter Terrorist Check (CTC), Security Check (SC) and Developed Vetting (DV). DV is required to work at the GCHQ.
I’m releasing a further article about improving extended validation further and that will go into more detail.
Personal note, I was saddened to hear the news that Gerv Markham cancer has reappeared and is incurable. My heart goes out to him and his family. The work Gerv has done has revolutionized this industry and will be remembered forever.
If you've got any questions at all, please email them to contact AT typewritten DOT NET.