This post is intended for a technical audience interested in how an EV SSL certificate can be used as an effective phishing device. I won't be held liable if someone uses this post for unlawful intentions. No one was harmed in this demonstration. Let's get on.
Extended validation or EV was designed back in the day to be an effective way to prevent phishing but, as we've seen through the years that extended validation has a lot of short comings such as long vetting processes, lack of wildcard support, and many other things. Now I'm going to demonstrate that it is indeed possible to phish with an EV SSL and how easy and straightforward it is to obtain the certificate. View Ryan Hurst's blog post here about the overall positive trust indicators in browsers.
First, I needed to think of a name which would be effective for phishing. After some deliberation, I chose the name "Identity Verified" as it would give the illusion to the user that the phishing site is safe.
Second, I had to think of a way of getting an EV SSL certificate for the intended name. After some research on the CA/Browser forum site, I found that, in the EV SSL certificate guidelines, section 8.5.2 stipulates that incorporated private entities are allowed to get hold of an EV SSL certificates. With that information in mind, I decided to incorporate a company here in the UK and after some more research, I found that a limited company by guarantee with the limited exemption was the right one but there was one catch; to incorporate a company in the UK, you need to have a verifiable address and valid ID. So what does an attacker do? Well they can purchase a valid stolen ID for a few pounds from the so called "Dark web" and just use, a service address as the address of the company and the director's home. These service addresses can be bought online for next to nothing.
Note: This company was made with a legitimate address and ID.
Now finally, I began searching for a company to incorporate this new company on my behalf and after a good hour of researching on Google, I found the right one. I won't say the company name here for legal purposes but I will say that the process was incredibly easy to do; no ID check to my knowledge and it costs less than £40. It took the next day for the company to be incorporated by Companies House.
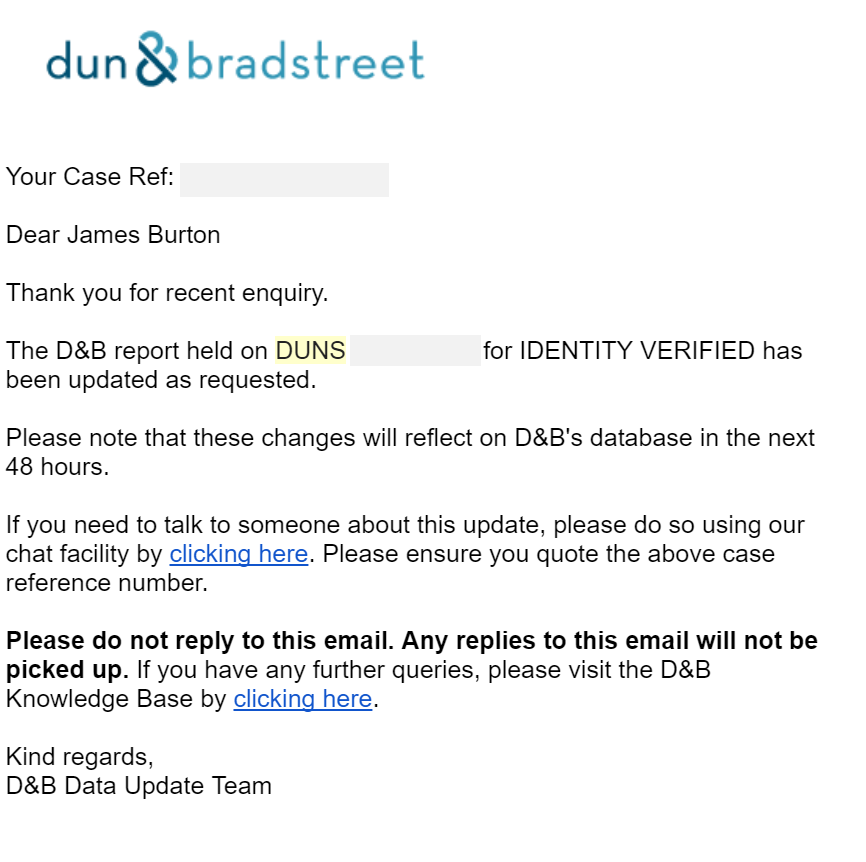
After all, this was finished, I now had to include a telephone number on a third party database as stipulated in section 11.5.2 of the EV SSL certificate guidelines. I chose Dun and Bradstreet as the third party database as it's extensively used by CAs for third party checking.
It was absolutely easy to add the extra information to Dun and Bradstreet database. I only needed to get my Dun and Bradstreet ID and fill in a form with my mobile number as the telephone and after a few days, it was included.
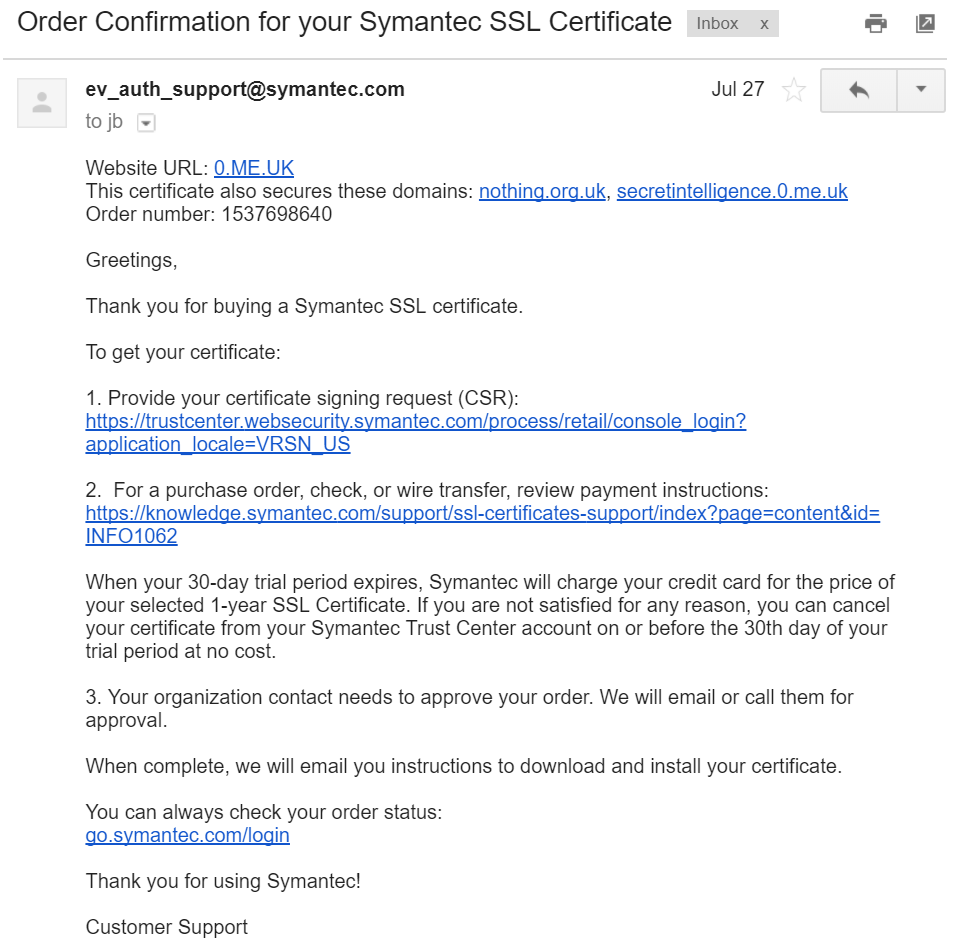
I'm ready to get an EV SSL Certificate. I chose Comodo and Symantec for this demonstration as they were that the time of this post the largest CAs in the industry.
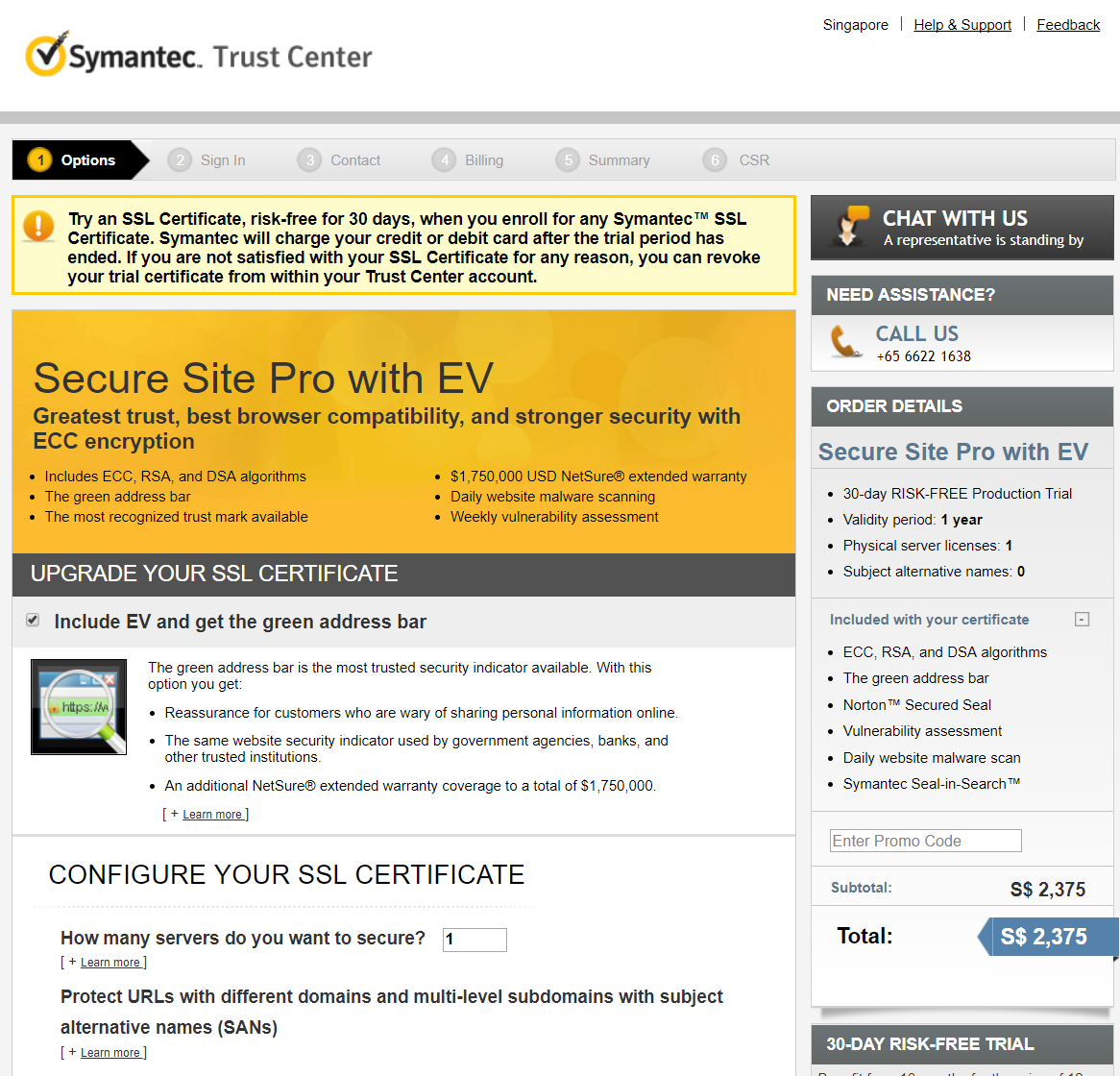
First, I went to Symantec site and found the 30 days free trial of production use EV SSL Certificate. After filling in all the details required by Symantec and including a 256-bit ECC CSR, I was finished for now until the validation process was completed.
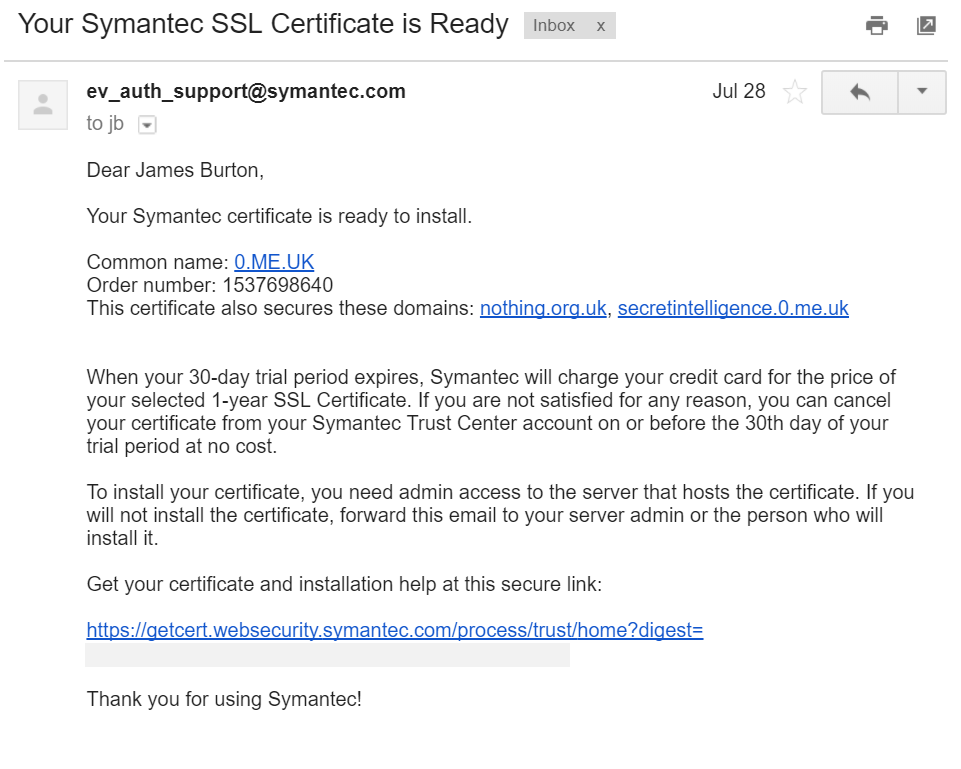
After a day and a bit of pushing the certificate was issued. You can view the issued extended validation SSL certificate on crt.sh: https://crt.sh/?id=181513189
After the successfully issued from Symantec, I then tried doing the same again from Comodo and it failed at the first hurdle. Richard Smith, who is the head of validation at Comodo felt that the certificate couldn't be issued due to compliance issues. Great job Richard!
Now the certificate part is finished, I can now get on with the phishing part of this test and demonstrate how someone could phish with an EV SSL. First I took a copy of both the Google and PayPal sites and then upload them sites onto nothing.org.uk. Now in a real world phish scenario, an attacker would need to also setup a database and etc to capture the data but I didn't need to because this wasn't an actual phishing attempt to capture real users' data.
In these screenshots below from Safari in OSX and IOS the chances of a successful phish are extremely high because of the way Safari hides the actual domain when the site is using an EV SSL and in, combination with the company name "Identity Verified" the site looks legitimate and safe.
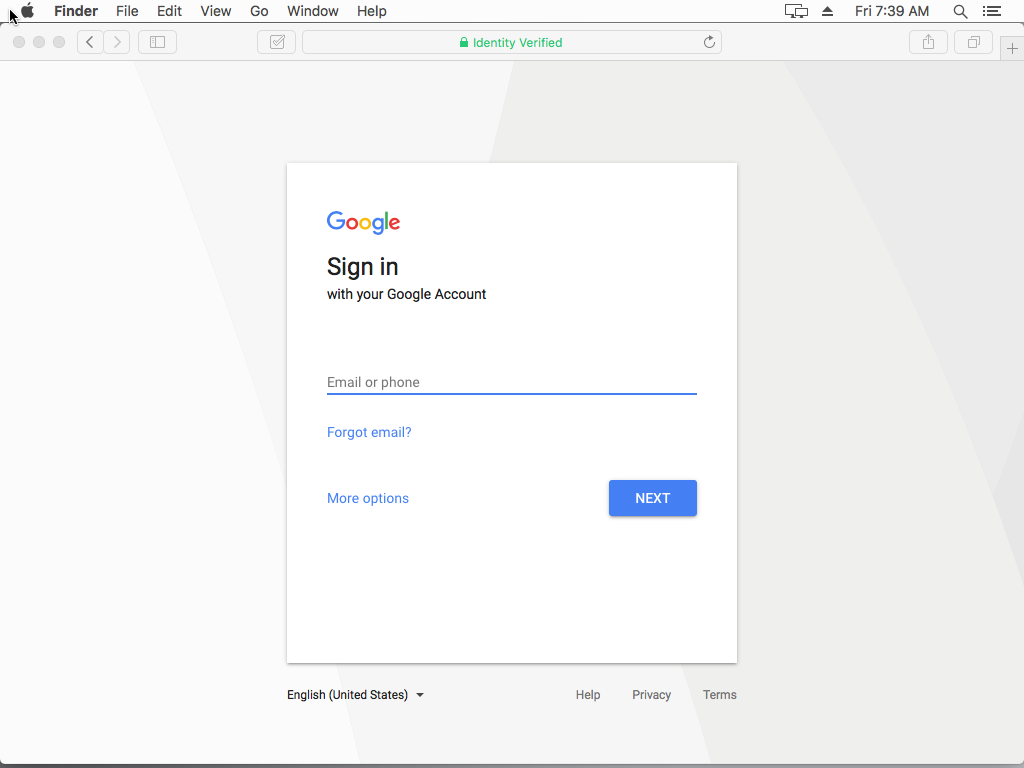
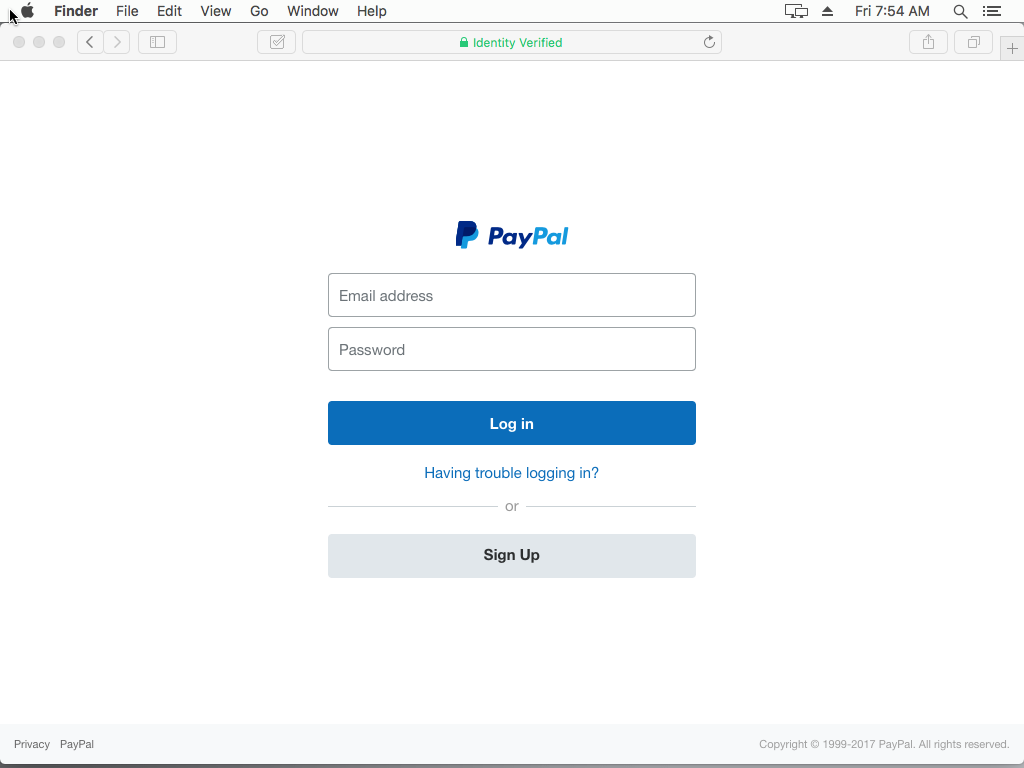
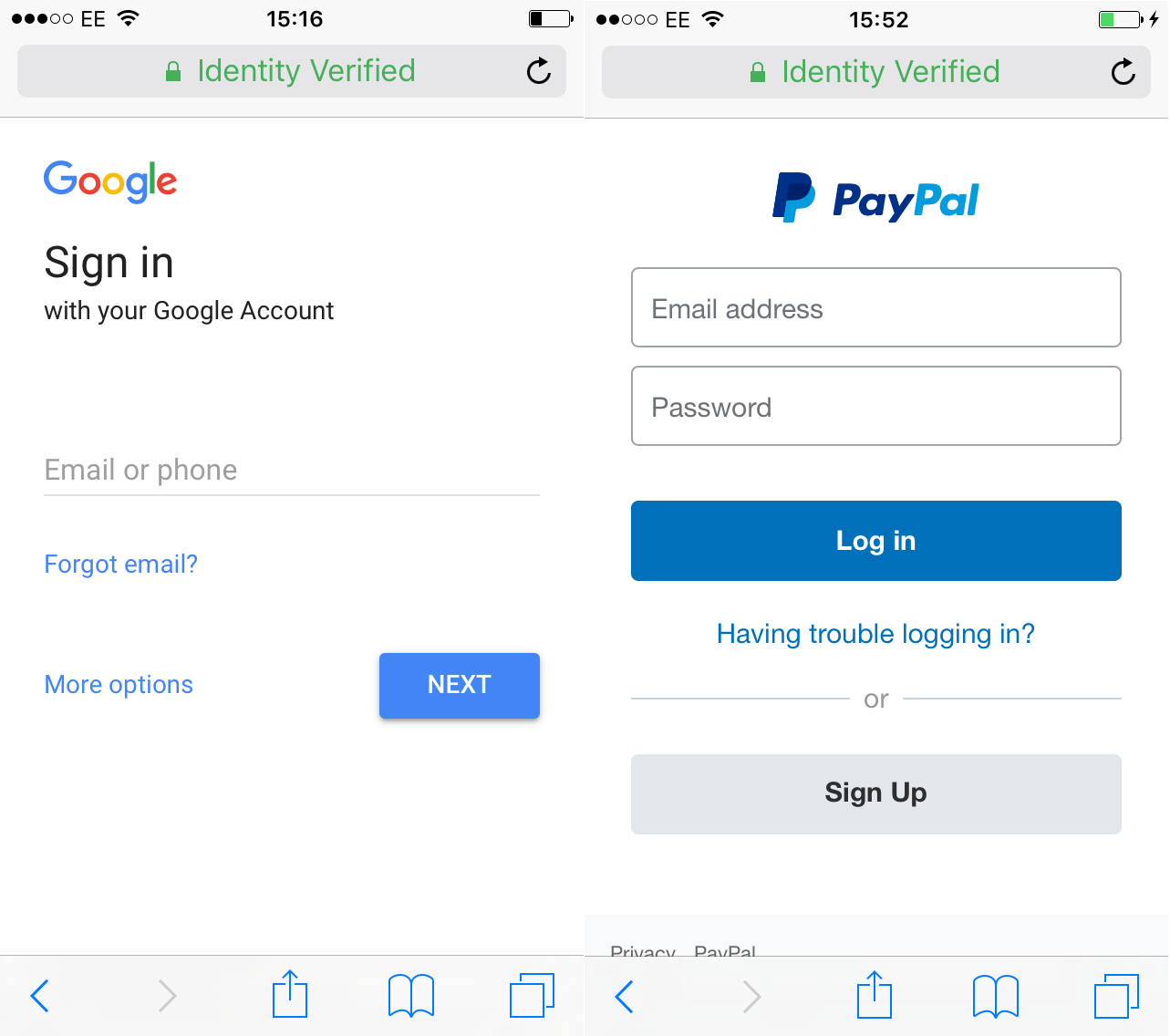
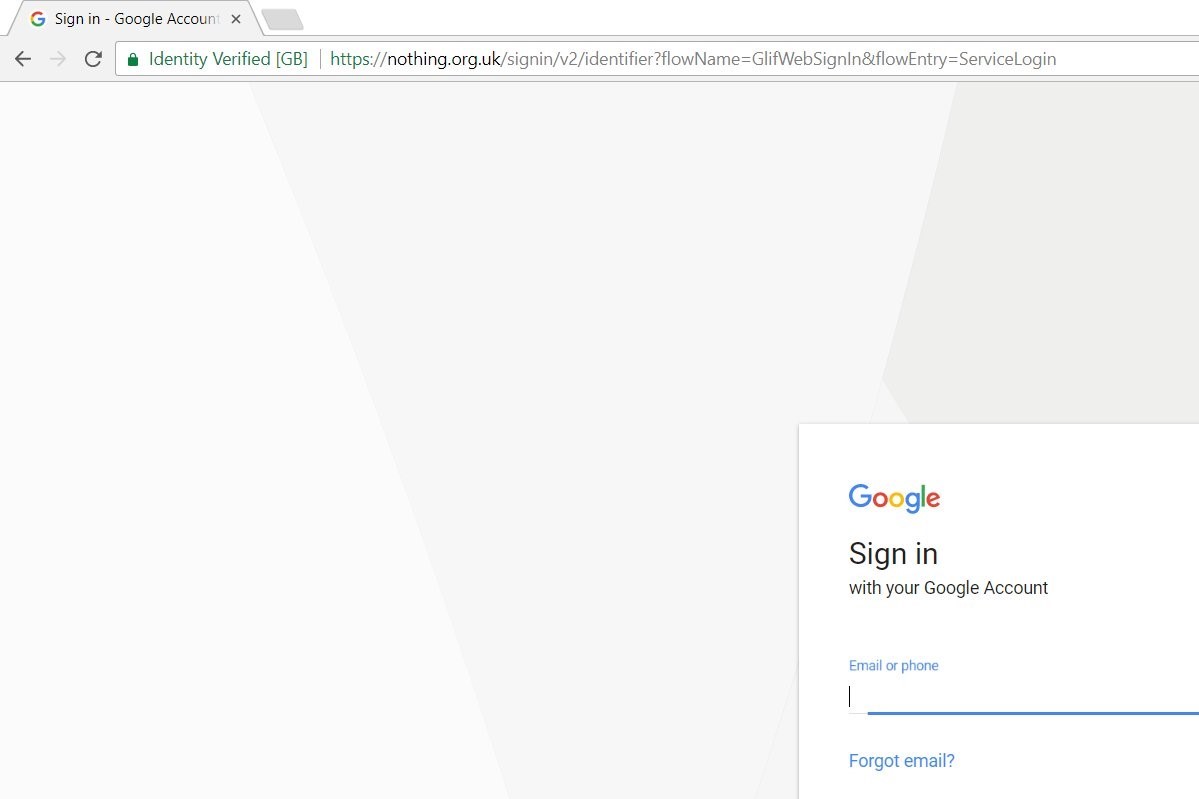
In this screenshot of Google Chrome, the domain name and the company name are clearly separated which can help the user identity if it's indeed a phishing site or not but if someone could get a hold of a short single letter like p.uk for PayPal or g.uk for Google the user would think that the company in question has moved over to smaller domain name and not be concerned.
A view of the certificate contents in Firefox.
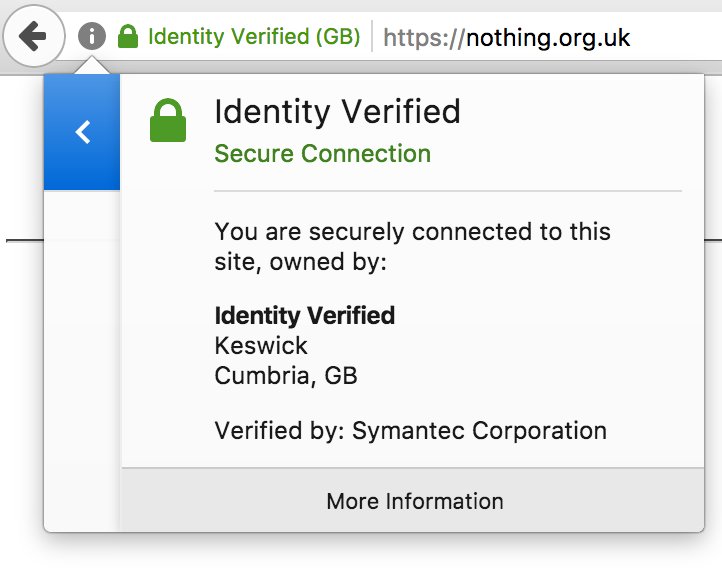
To conclude this post, I think Symantec shouldn't have issued this EV SSL certificate in the first place as the company name was too common and could easily be misconstrued in the browser.
Update (5th May 2018): My opinion has since changed.
The EV guidelines are not up to par and can be easily circumvented. Stringent vetting on both the applicant and the company are necessary and this will provide additional assurance that the EV cert won't be used for harmful purposes. If the EV cert was ever used for harmful purposes the investigators can easily obtain the necessary details and prosecute the offenders if guilty.
In this case, the CA should've been more cautious in issuing this EV cert and should've required extra details from the applicant to make sure that this particular EV cert would not be used for harmful purposes.
Check out Ian's Extended Validation is Broken article. This article enhances this research and shows different way to effective phish users.